Proven protection for confidential data, device access and network safeguards
Physical Security Threats
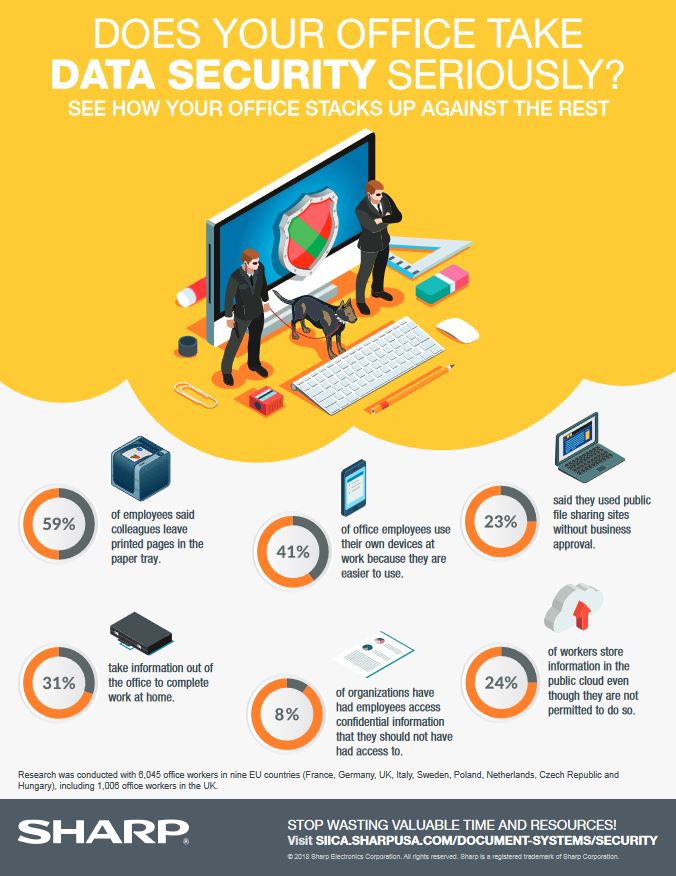
Typically, MFPs are located in areas accessible by multiple people. Unauthorized personnel can potentially access corporate networks when devices are not fully protected. In addition, any information stored on a local desktop computer or a server can be printed without authorization. Meanwhile, at the device, confidential information can be accidentally or even purposely copied from stored documents, taken from the output tray or faxed without authorization.
Network Security Threats
Unsecured access to a company’s stored data makes it vulnerable to being stolen or altered. In the worst case, a user from the outside can obtain confidential information, unleash a Denial of Service (DOS) attack, or even place a virus on the device via a network or a phone line. Through a fax line, or corporate LAN, communications could be intercepted or sent without permission anywhere in the world. Even MFP data stored on a hard disk drive or in memory could be compromised or stolen if not protected.
Security Downloads
Sharp Security Suite
Sharp helps IT administrators and organizations achieve optimal document security through the Sharp Security Suite. The Sharp Security Suite is effective at helping prevent unauthorized access to your network and your most confidential information. Sharp MFPs utilize a multi-layered approach for protection—providing exceptional and extensive control over the users, devices, ports, protocols and applications that access Sharp MFPs on your network.
The Sharp Security Suite includes:
- Sharp MFP standard security features
- Sharp’s Data Security Kit (Commercial and Common Criteria Certified versions)
- Print driver security features
- Sharp OSA technology-enabled security applications
Sharp Data Security

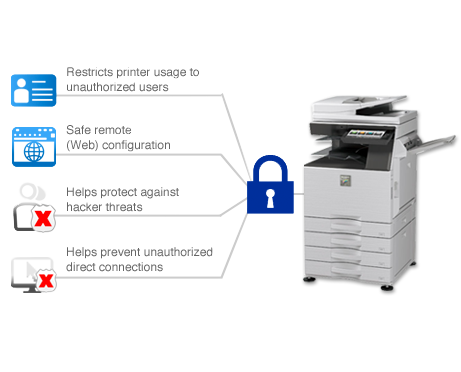
Sharp Network Interface
Threats to data and information can result from unauthorized access to the MFP or printer, or by various forms of malicious network intrusion attempts and hacks.
Sharp MFPs’ intelligent network interface provides an extensive set of access and network control security features designed to prevent these threats as well as document improper device access.
- Access Control Security
- Data And Information Security
- Network Security
- Fax Security
- Audit Trail Security
- Document Security
Security Standards
Please share this page: